Explained: InterPlanetary File System (IPFS)

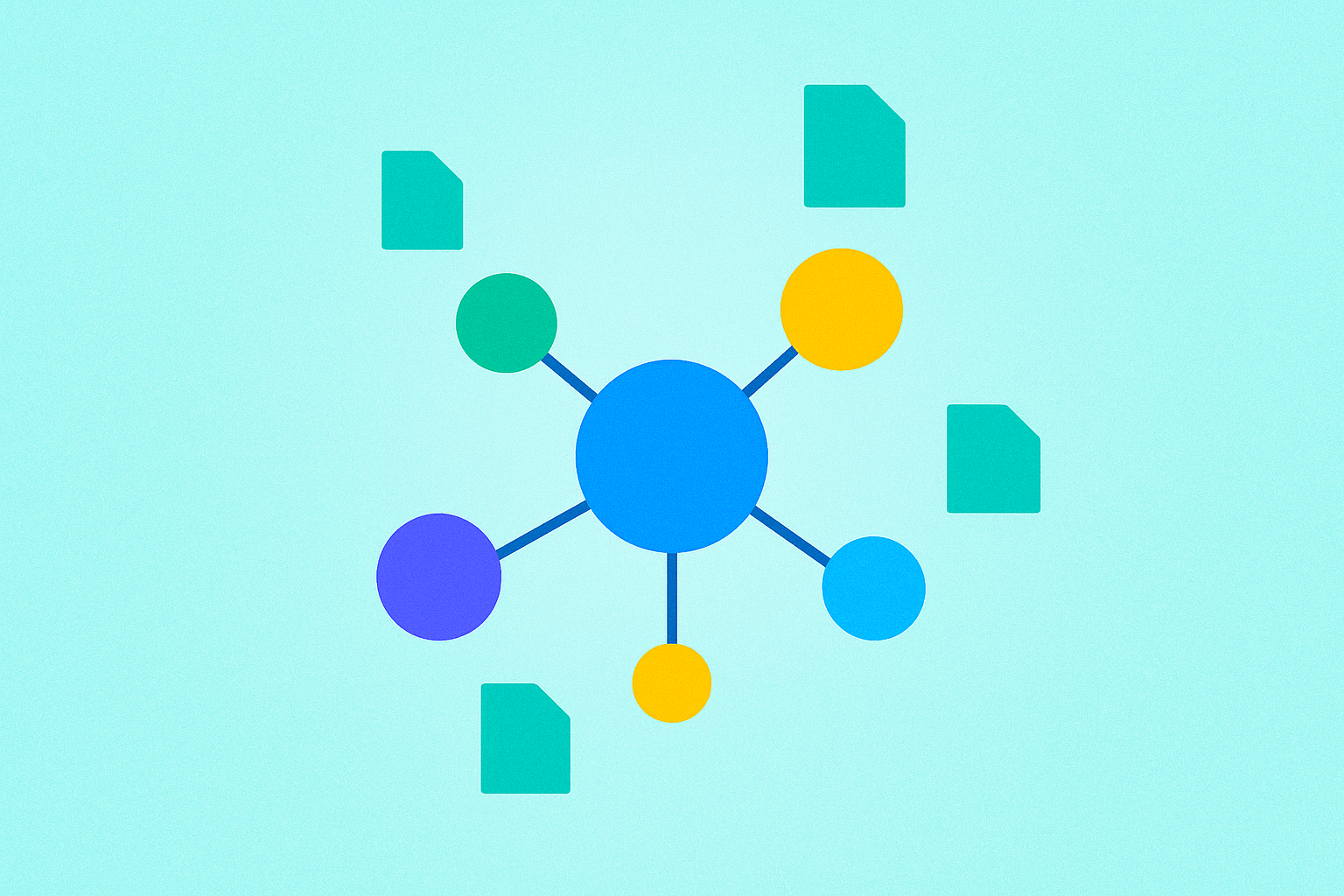
What Is IPFS?
IPFS is a protocol that enables users to store and share files in a distributed, peer-to-peer manner. Unlike traditional centralized file sharing systems that rely on a single server or location, IPFS distributes files across multiple nodes in a network, allowing them to be retrieved from any participating peer.
The protocol utilizes a unique addressing system called Content Addressed Storage (CAS) to identify and retrieve files. When a user adds a file to IPFS, the system assigns a unique cryptographic hash based on the file's content. This hash serves as the file's permanent address, enabling any user to retrieve the file by requesting it using this hash. This content-based addressing approach ensures that files are immutable and verifiable, as any change to the file content would result in a different hash.
Benefits of IPFS
IPFS offers several significant advantages that distinguish it from traditional file sharing methods:
Decentralization: IPFS is fundamentally a decentralized system where files are stored and shared among multiple nodes throughout the network. This distributed architecture eliminates the single point of failure present in centralized systems, making the network more resilient to censorship and server failures. No single entity controls the network, ensuring greater freedom and independence.
Faster Speeds: IPFS can deliver files significantly faster than traditional file sharing methods by enabling simultaneous downloads from multiple peers. When a user requests a file, the system retrieves blocks from various nodes in parallel, substantially reducing bandwidth bottlenecks. This approach also distributes the load across the network, reducing strain on individual servers and making the overall web infrastructure more efficient and responsive.
Increased Security: IPFS employs cryptographic hashing to guarantee the integrity and authenticity of files. Every file is cryptographically verified through its content hash, making it virtually impossible to tamper with files without detection. This security model is inherently more robust than traditional file sharing methods, which remain vulnerable to attacks such as man-in-the-middle attacks, file tampering, and unauthorized modifications.
How Does IPFS Work?
IPFS operates by fragmenting files into smaller units called "blocks," which are then distributed across multiple nodes within the network. When a user requests a file, IPFS retrieves these blocks from various nodes and reassembles them into the original file. The system maintains a distributed hash table that tracks which nodes store which blocks, enabling efficient file location and retrieval across the network.
A key feature of IPFS is its "pinning" mechanism, which allows users to store files on their own nodes permanently. When a file is pinned, it remains available on the network even if the original uploader goes offline. This ensures persistent availability and prevents important files from disappearing due to node failures or network changes. Users can configure their nodes to pin specific files, effectively participating in the network's distributed storage infrastructure.
Conclusion
IPFS represents a transformative technology with the potential to fundamentally reshape how files are stored and shared across the internet. Its decentralized and distributed architecture provides superior resilience against censorship and infrastructure failures, while its innovative content-addressed storage system and caching mechanisms deliver enhanced performance and efficiency.
The adoption of IPFS continues to grow across various applications and use cases, from decentralized web hosting to distributed content delivery. As the technology matures and integrates further with existing web infrastructure, IPFS demonstrates the viability and benefits of decentralized file systems. The protocol exemplifies a shift toward a more open, resilient, and user-controlled internet architecture, where data ownership and accessibility are distributed rather than concentrated in the hands of centralized service providers.
FAQ
What is IPFS (InterPlanetary File System)? What are its core concepts?
IPFS is a decentralized file storage protocol using content-based addressing. Core concepts include peer-to-peer distribution, immutable hashing, and distributed storage. Files are identified by hash rather than location, enabling censorship-resistant, efficient data sharing across global networks.
What are the advantages of IPFS compared to traditional HTTP and cloud storage?
IPFS offers decentralized file storage with no single point of failure, faster content delivery through peer-to-peer networks, permanent file addressing via content hashing, reduced bandwidth costs, and enhanced data ownership and privacy compared to centralized cloud storage solutions.
How does IPFS work? What are the principles of content addressing and distributed storage?
IPFS uses content addressing to identify files by their hash rather than location. Files are split into blocks, hashed, and stored across distributed nodes. Users retrieve content by its cryptographic hash, enabling peer-to-peer file sharing without central servers. This ensures data persistence, censorship resistance, and efficient bandwidth usage across the network.
How to store and retrieve files using IPFS?
Upload files to IPFS nodes, receiving a unique content hash. Share this hash with others to retrieve files peer-to-peer. Files are distributed across the network, ensuring decentralized access without relying on centralized servers.
What are the practical applications and use cases of IPFS?
IPFS enables decentralized file storage, content distribution, dApp hosting, NFT metadata storage, and censorship-resistant media sharing. It powers Web3 infrastructure, archiving, and peer-to-peer data exchange across blockchain ecosystems.
Is data stored on IPFS secure? How is data privacy protected?
IPFS uses content addressing and cryptographic hashing for integrity verification. Files are immutable once stored. For privacy, use encryption before uploading. IPFS itself doesn't encrypt data, so sensitive information requires client-side encryption for protection.
What is the relationship between IPFS and blockchain technology?
IPFS serves as a decentralized storage layer for blockchain applications. It stores large data files off-chain while blockchain records content hashes, enabling efficient data management. Together they create trustless, distributed systems where blockchain ensures data integrity and IPFS provides scalable storage infrastructure.
What are the hardware requirements for using IPFS? How to set up an IPFS node?
IPFS requires minimal hardware: a modern CPU, 2GB+ RAM, and stable internet connection. To set up a node, download IPFS binary or Docker image, initialize with 'ipfs init', then run 'ipfs daemon'. Connect to the peer-to-peer network and start storing or retrieving distributed content.

XZXX: A Comprehensive Guide to the BRC-20 Meme Token in 2025

Survey Note: Detailed Analysis of the Best AI in 2025

Detailed Analysis of the Best 10 GameFi Projects to Play and Earn in 2025

Kaspa’s Journey: From BlockDAG Innovation to Market Buzz

Best Crypto Wallets 2025: How to Choose and Secure Your Digital Assets

Popular GameFi Games in 2025

Gate Ventures Weekly Crypto Recap (March 2, 2026)

Gate Ventures Weekly Crypto Recap (February 23, 2026)

Gate Ventures Weekly Crypto Recap (February 9, 2026)
What is AIX9: A Comprehensive Guide to the Next Generation of Enterprise Computing Solutions

What is KLINK: A Comprehensive Guide to Understanding the Revolutionary Communication Platform







