Adam Back: Bitcoin Can Combat Quantum Threats Through Soft-Forks


Bitcoin's Quantum-Resistant Approach Through Soft-Forks
Blockstream CEO Adam Back has stated that Bitcoin can adapt to future quantum computing threats through soft-fork upgrades, ensuring its long-term security. In a recent statement, Back emphasized that while quantum threats are not anticipated for the next 20 to 40 years, Bitcoin's existing upgrade mechanisms are already capable of implementing quantum-resistant solutions without disrupting the network.
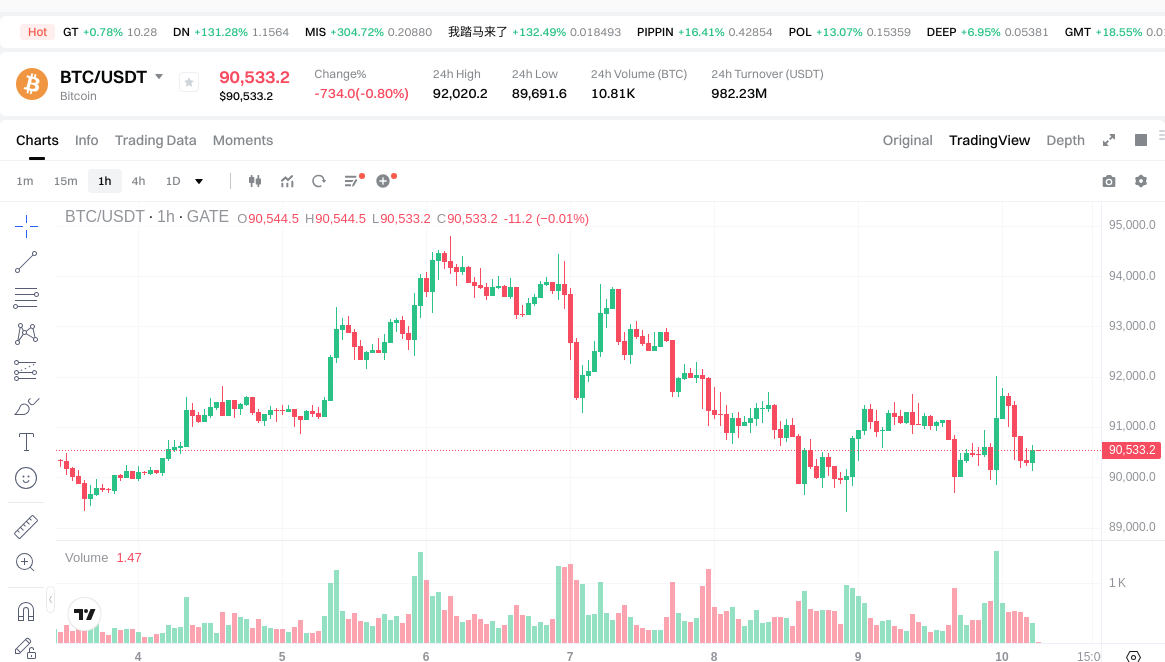
Soft-forks represent a backward-compatible upgrade method that allows Bitcoin to introduce new features while maintaining compatibility with older versions of the protocol. This approach is particularly valuable for implementing quantum-resistant cryptographic signatures, as it enables the network to evolve gradually without forcing all participants to upgrade simultaneously. The flexibility of soft-forks ensures that Bitcoin can respond to emerging security challenges while preserving the stability and continuity that users depend on.
Understanding the Timeline and Technical Solutions
Back highlighted that quantum computing poses a theoretical threat to Bitcoin's cryptographic foundations, but the timeline for such threats becoming practical remains distant. Current estimates suggest that quantum computers capable of breaking Bitcoin's encryption are unlikely to emerge for several decades. This extended timeline provides the Bitcoin community with ample opportunity to implement and test quantum-resistant solutions.
One of the key technical solutions mentioned is the SLH-DSA (Stateless Hash-Based Digital Signature Algorithm) standard developed by NIST (National Institute of Standards and Technology). This cryptographic scheme is specifically designed to resist attacks from quantum computers by relying on hash functions rather than mathematical problems that quantum computers could potentially solve efficiently. By integrating SLH-DSA or similar quantum-resistant algorithms, Bitcoin can enhance its cryptographic signatures to protect against future quantum threats.
The implementation of these advanced cryptographic methods through soft-forks means that Bitcoin can maintain its security posture without requiring a complete overhaul of the network. Users who continue to operate older nodes would still be able to validate transactions, while those who upgrade would benefit from enhanced quantum-resistant security features.
Bitcoin's Modular Evolution and Network Security
Back emphasized Bitcoin's robust infrastructure by citing past successful upgrades, particularly the Taproot activation. Taproot, which was implemented through a soft-fork, demonstrated the network's capacity for modular and secure evolution. This upgrade introduced more efficient and private transaction methods while showcasing the Bitcoin community's ability to coordinate complex technical improvements.
The Taproot example illustrates several important principles that apply to future quantum-resistant upgrades. First, it shows that the Bitcoin network can achieve consensus on significant technical changes through its established governance mechanisms. Second, it demonstrates that upgrades can be implemented smoothly without causing network disruptions or splitting the blockchain. Third, it proves that Bitcoin's development process is mature enough to handle sophisticated cryptographic enhancements.
This adaptability positions Bitcoin favorably for integrating quantum-resistant cryptography when necessary. The network's track record of successful upgrades provides confidence that future implementations of quantum-resistant algorithms will be executed with similar care and effectiveness. Back's observations underscore that Bitcoin's security model is not static but rather designed to evolve in response to changing technological landscapes.
The modular nature of Bitcoin's upgrade process also means that quantum-resistant features can be introduced incrementally, allowing for thorough testing and gradual adoption. This measured approach reduces the risk of introducing vulnerabilities while ensuring that the network remains secure against both current and future threats. As quantum computing technology continues to develop, Bitcoin's flexible upgrade framework ensures that appropriate countermeasures can be deployed in a timely and effective manner.
FAQ
What are the specific threats quantum computing poses to Bitcoin's security?
Quantum computing threatens Bitcoin by potentially breaking elliptic curve cryptography used in digital signatures. Attackers could harvest public keys now and decrypt them later. Bitcoin's Taproot upgrade provides technical pathways for quantum-resistant upgrades, though full implementation requires years. Post-quantum cryptography standards are being developed to mitigate risks.
How does Adam Back believe soft forks can help Bitcoin combat quantum threats?
Adam Back believes soft forks enable Bitcoin to implement quantum-resistant cryptographic upgrades through mechanisms like Taproot, allowing adaptive defenses against quantum computing threats without requiring hard forks.
How long will it take for Bitcoin to implement these quantum protection measures?
Bitcoin is estimated to require 5-10 years to implement quantum-resistant measures through soft-forks. While near-term quantum threats are minimal, proactive preparation is essential for long-term security. The transition process may begin within the coming years.
Why is soft fork a better choice than hard fork in combating quantum threats?
Soft forks maintain network compatibility and stability by allowing old nodes to validate new quantum-resistant transactions without splitting the network. Unlike hard forks, they enable gradual, consensus-based upgrades, ensuring smoother community adoption and reducing the risk of network fragmentation during critical security transitions.
How vulnerable is Bitcoin's current cryptographic algorithm to quantum computers?
Bitcoin's ECDSA algorithm is theoretically vulnerable to quantum computers through Shor's algorithm, which could break it. However, current quantum computers lack sufficient power to pose an immediate threat. Bitcoin can implement soft-forks to upgrade its cryptographic standards before quantum computers become practically capable.
How do other blockchain projects address quantum computing threats?
Other blockchain projects deploy post-quantum checkpoints and quantum-resistant algorithms. Cardano uses Mithril protocol, while others explore similar technologies to protect blockchain security against quantum threats.

Bitcoin Post-Quantum Cryptography Migration: Timeline and Security Solutions for Quantum Computing Threats

The post-quantum migration of Bitcoin may take 5 to 10 years, what needs to change first?

Jack Dorsey's Net Worth in 2025: Crypto Investments and Web3 Impact

How Many Nodes in Bitcoin

How Did Dan Bilzerian Make His Money

What Does BTC Mean in Text

JPMorgan Chase, Cryptocurrency ETFs, and the De-Risking Phase in Crypto Markets

Trump, SBF, FTX, and the Pardon Debate in US Crypto Politics
Trump, Crypto Platform, and the Push for a US Crypto Bank License

Bitcoin Price Drops Below 90,000 as Liquidations Surge Across the Crypto Market

Dow Jones Record: Dow Hits 49,000 as Stock Market Rally Accelerates







